I’m seeing a weird connection issue with WPA3 settings -
SSID Config:
Enterprise Network w/Radius Auth
Fast Roaming: ON
PMF: ON
BSS Transition: ON
If I set WPA3 to “ON” then our Windows laptops connect via WPA3-Enterprise no problem. iOS devices usually choose WPA2-Enterprise.
I wanted everything to use WPA3 so if I set WPA3 to “Required” then the iOS devices connect via WPA3-Enterprise but the Windows laptops can’t connect.
Any ideas why that may be?
@benmott I’ve had some strange behavior with iOS devices if I don’t wait long enough after changing the security type. Sometimes it helps to delete the old WiFi profile as well. How long did you wait, and did you try deleting the old profile?
We currently support WPA2/3-Enterprise (on) or WPA3-Enterprise 192-bit mode (required), the latter of which would come down to client driver support. We don’t actually have a way to enable plain WPA3-Enterprise only at the time of writing this reply.
I take back my prior comment about 11r with 192-bit mode, however FT isn’t actually being provisioned at this time when WPA3 is set to required. That looks like something we can change, although probably should make sure it’s supported/working as intended first. Client support likely will widely vary (favouring newer devices)
There is a way to manually make an SSID operate in WPA3-Enterprise only mode, but it’s not officially supported.
EDIT: Minor additions/adjustments for clarity. EDIT2: Major correction.
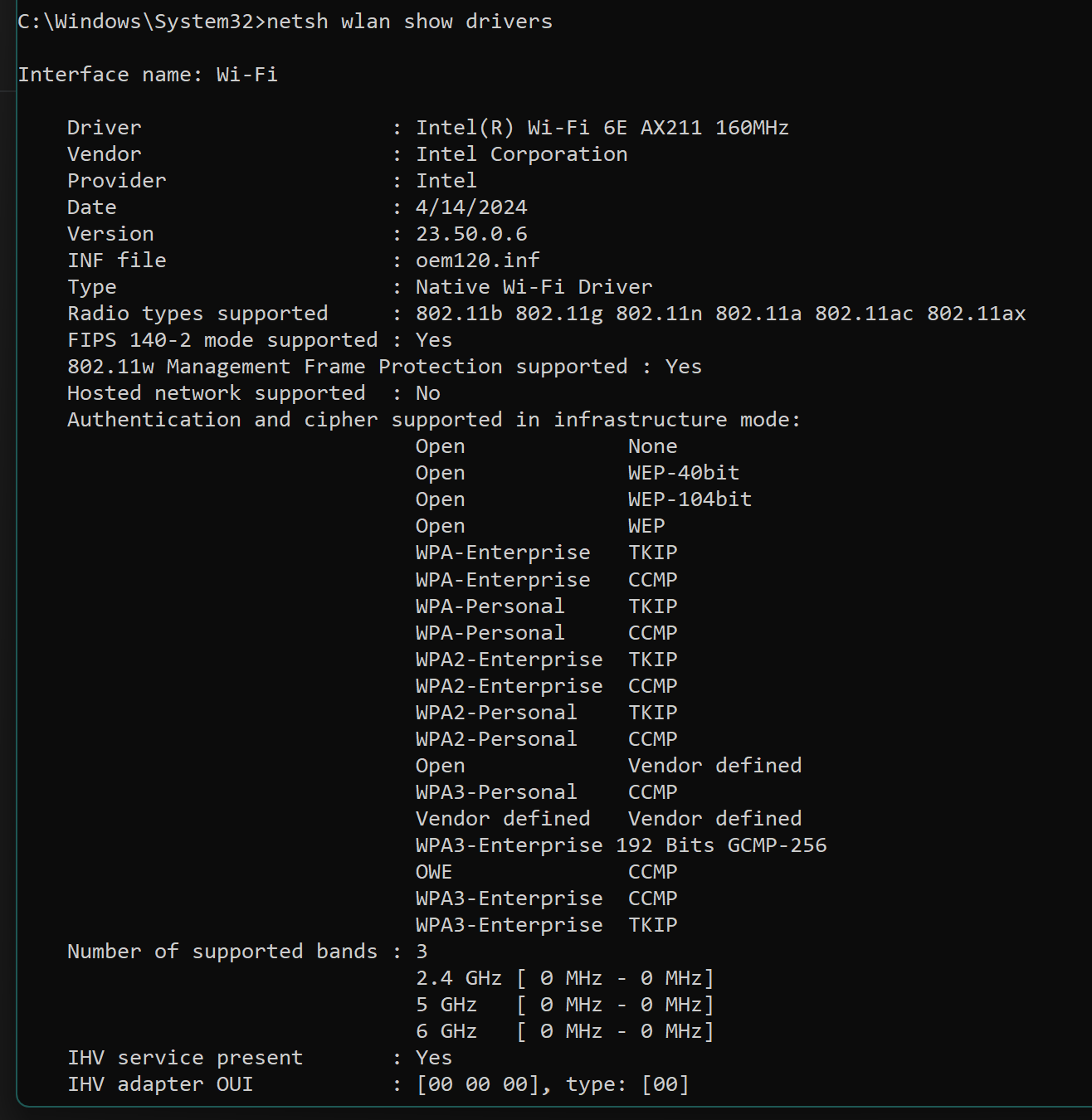
I checked the laptop driver and it shows it should be compatible with the 192-bit mode -
With that shouldn’t it be able to connect on the Windows laptop if it shows that it’s a supported auth method?
I have the wifi profile in an iOS MDM profile so it’s not able to be deleted (without removing the profile). The profile security type is set to WPA3-Enterprise, but it seems to be falling back to WPA2-Enterprise when the setting is “On” but will automatically work with the WPA3 if set to “Required” with no issue (but then Windows laptops don’t work even though they should support 192-bit security (see my response to MikeD). This occurs with all my iOS devices on the network - not just one. May it be an issue of iOS and not the AP?
If the drivers says it supports it then it should work. Sometimes it could still be a driver issue, but (far) less likely in that case. On our end when enabling 192-bit mode we are setting GCMP-256 as the pairwise cipher (which is what listed there).
Were the windows laptops ever connected when WPA3 was set to On? If so, did you delete the profile before trying to connect when it was set to required? If you did not, then it could be as simple as that. Windows still seems to be the worst for profile management, although none are necessarily great when they encounter a mode change.
If that has been done and didn’t help, then reviewing the logs from both the AP during time of connection attempt, and maybe also check the Windows Event Viewer.
- Press Win + X, or right click on Start, and choose Event Viewer.
- Expand Windows Logs, and choose System.
- Select ‘WLAN-AutoConfig’, ‘WiFiNetworkMgr’, and ‘Microsoft Windows WLAN Dialog’ from Event Sources drop down.
These may give a hint as to why it’s not working.
On the AP the logs can be found at /var/log/messages (for current/latest, further back may be message.0 or messages.1). If you want to connect via shell, and then just type logs, you can watch in real time another system while your testing (assuming you have one handy). Again check during the time of the connection attempt, and it may give some indication of why it’s failing to connect.
On my iPhones I usually notice them reporting WPA2-Enterprise when it’s WPA2/3 mixed mode; it has been that way across multiple vendors, with profile rebuilds. I haven’t spent any time looking into it before, but I’ll do so later. Maybe there is a way to improve it’s likelihood to transition to WPA3. I’ll follow up.