I’m in the midst of fiddling with VLAN and port tagging and I’m very confused. I get strange outcome on VLAN listed per device.
VLAN 90, 192.168.90.1/24, setup as Isolated, and firewall rule allowing traffic from 192.168.90.0/24 LAN to WAN (may not be necessary?). The purpose is to keep my old router underneath the Route10 for the time I’m migrating devices, while still allowing access to internet, and for learning how to set up VLANs as well.
Furthermore:
Short lease time, 60 s, setup for VLAN 1 and 90 for testing.
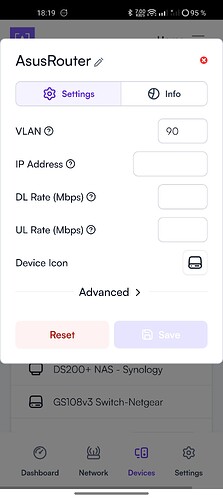
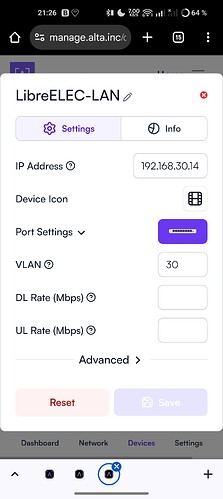
Device (Asus router) → VLAN 90, IP Static 192.168.90.2 (and left blank in a second try)
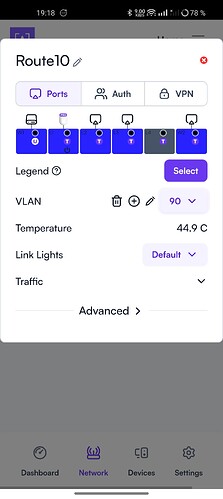
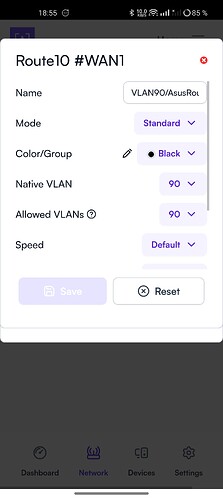
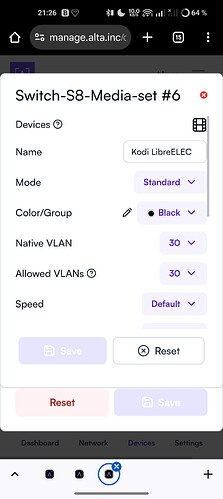
Route10, WAN#1 (first port from the left) → Mode Standard, Color Black, Native VLAN 90, Allowed VLANs 90 only.
Port shows as U for VLAN 90 in Route10 ports layout.
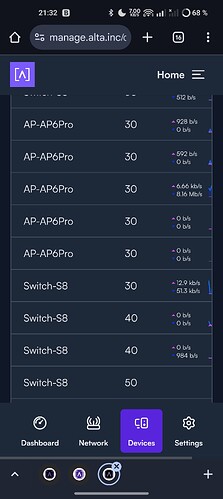
I get access to Internet through my old router, IP shows as intended (also with dynamic IP in the correct VLAN subnet) but in the devices list I get VLAN printed as 2. Anyone with comments on that? Seems like a bug in the printout or does it reside in a VLAN 2 that is not even defined?!
Also, if I set Devices VLAN to blank (remove 90) the connection to the Router is lost. It seems like blank is interpreted as Default VLAN 1 (?), as the corresponding Route10 Native VLAN is reverted to Default at the same time.
Then, if I change the Route10 port Native VLAN to 90 again I regain access. But, I would have thought that any device attached to the Untagged port assigned for VLAN 90 traffic would show up automatically on VLAN 90 with IP in the corresponding subnet. Is this also a potential bug or have I misunderstood it all?
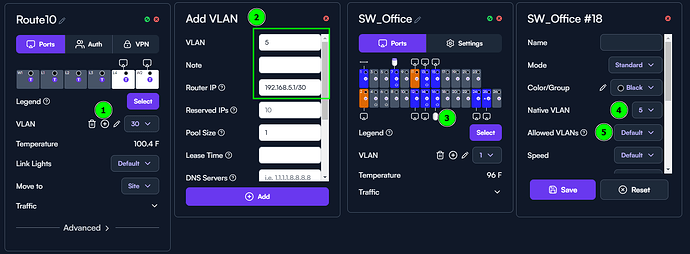
When I try the same maneuver for a VLAN 30, also short lease time but not Isolated, for two streaming devices attached to an unmanaged switch connected to Route10 I end up with them on the correct subnet for dynamic IP, corresponding to VLAN 30, but they show up as VLAN 1 in the devices list. ![]() Hmmm?
Hmmm?
All WiFi devices shows up with correct VLAN corresponding to VLAN setup per WiFi SSID.