I’ve noticed port 53 being publicly available on the WAN IP address - firewall rules for explicitly blocking this seem to be ignored as well. Anyone faced this already?
Even with the default rules, the only thing I see open in 1-1024 range on tcp or udp is 500/udp which is one of the default rules, so expected.
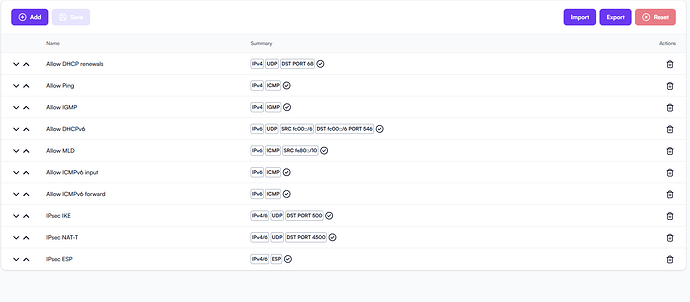
My current rules:
Here’s the results of my nmap scan:
What type of WAN connection do you have? How are you checking that this port is open? For the latter question, I don’t just mean what software, I also mean are you testing from a local computer that is behind the Route10? Or a completely external host?
I’ve restarted my router and can’t reproduce it anymore ![]() - might’ve been a bug, in case it comes up again I’ll reach out to support for a live analysis.
- might’ve been a bug, in case it comes up again I’ll reach out to support for a live analysis.
For the record, it’s been publicly reachable, I’ve tested from one of my remote servers.
Before rebooting I checked the firewall rules for zone_wan_input and port-forwardings:
root@oasis-gw:~# iptables -L zone_wan_input
Chain zone_wan_input (1 references)
target prot opt source destination
input_wan_rule all -- anywhere anywhere /* !fw3: Custom wan input rule chain */
ACCEPT udp -- anywhere anywhere udp dpt:bootpc /* !fw3: Allow DHCP renewals */
ACCEPT icmp -- anywhere anywhere icmp echo-request /* !fw3: Allow Ping */
ACCEPT igmp -- anywhere anywhere /* !fw3: Allow IGMP */
ACCEPT udp -- anywhere anywhere udp dpt:isakmp /* !fw3: IPsec IKE */
ACCEPT udp -- anywhere anywhere udp dpt:4500 /* !fw3: IPsec NAT-T */
ACCEPT esp -- anywhere anywhere /* !fw3: IPsec ESP */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */
MINIUPNPD all -- anywhere anywhere
MINIUPNPD all -- anywhere anywhere
zone_wan_src_DROP all -- anywhere anywhere /* !fw3 */
root@oasis-gw:~# iptables -t nat -L zone_wan_prerouting
Chain zone_wan_prerouting (1 references)
target prot opt source destination
prerouting_wan_rule all -- anywhere anywhere /* !fw3: Custom wan prerouting rule chain */
DNAT tcp -- anywhere anywhere tcp dpt:ssh /* !fw3: ssh */ to:192.168.1.24:22
DNAT udp -- anywhere anywhere udp dpt:80 /* !fw3: http-nextcloud */ to:100.64.0.101:80
DNAT tcp -- anywhere anywhere tcp dpt:www /* !fw3: http-nextcloud */ to:100.64.0.101:80
DNAT tcp -- anywhere anywhere tcp dpt:https /* !fw3: https-nextcloud */ to:100.64.0.101:443
DNAT udp -- anywhere anywhere udp dpt:7777 /* !fw3: s7777 */ to:100.64.0.110:7777
DNAT tcp -- anywhere anywhere tcp dpt:7777 /* !fw3: s7777 */ to:100.64.0.110:7777
DNAT tcp -- anywhere anywhere tcp dpt:51821 /* !fw3: wg*/ to:192.168.50.5:51821
DNAT udp -- anywhere anywhere udp dpt:51821 /* !fw3: wg*/ to:192.168.50.5:51821
MINIUPNPD all -- anywhere anywhere
MINIUPNPD all -- anywhere anywhere
Eh, that’s too bad, but on the same hand, I’m glad it’s properly closed post-reboot. I thought maybe you were testing from behind the Route10, but if you aren’t seeing it post reboot, that rules that out.
Please don’t hesitate to reach out if it happens again. I’ll send you my email via DM.
EDIT: Sorry, forgot to mention. Based on the rules shown, it shouldn’t be allowed. However, there is one exception—I see UPnP running, which could open that port if a client requests it.