Is there official documentation on the ports, protocols and services (PPS) required through a firewall to allow the access points to communicate with on-prem controllers as well as cloud controllers?
I would like this as well!
I can gather them from my Palo but I’d prefer if the team had official documentation.
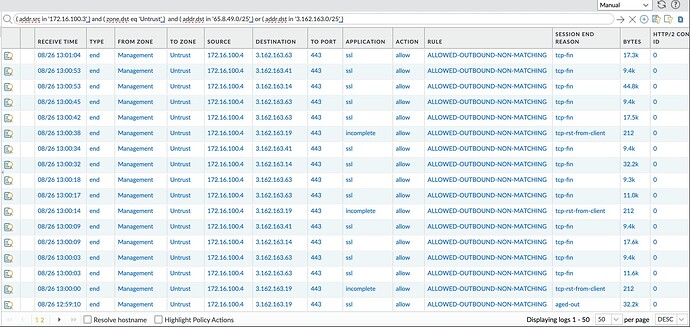
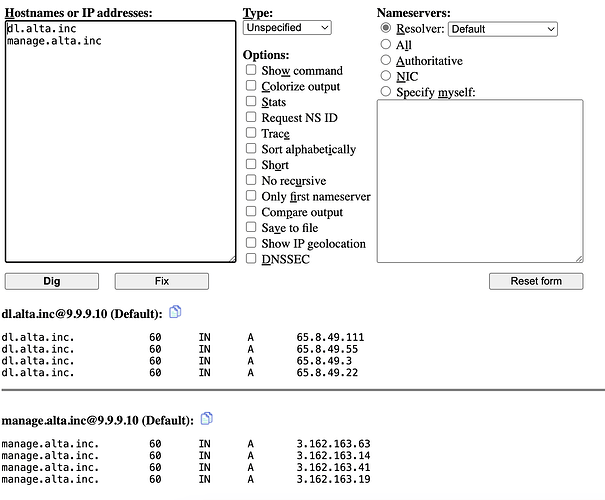
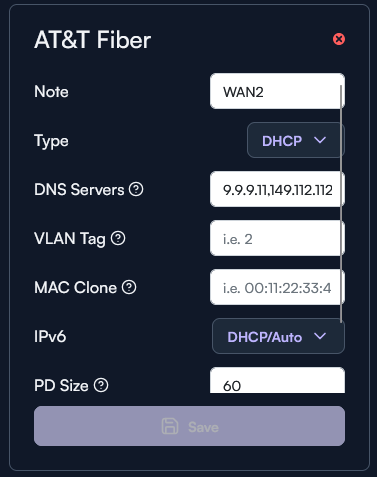
Not official, but port 443 to the desired controller (cloud controller is manage.alta.inc), as well as port 443 for dl.alta.inc for firmware updates should be the main two hosts and ports you will need. You will always want NTP and DNS open.
-Jeff
So tcp/443, udp/123, tcp/53 and udp/53.
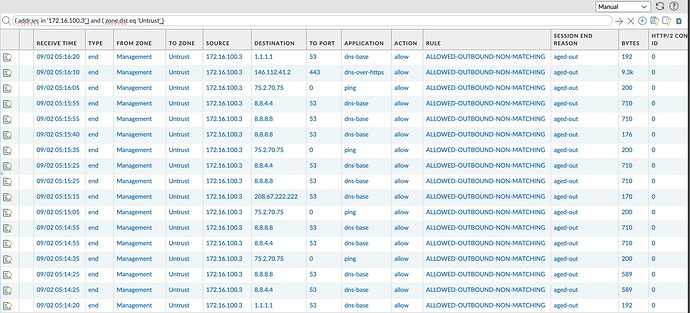
Seeing a lot more traffic reaching out to end points other than what you’ve listed above. A lot of dns-over-https and the use of DNS servers other than the ones I’ve hardcoded on the access point…
Last connection on 8/26/2024
You’ll need ping.alta.inc as well. That’s the 75.2.70.75 address. Every 30 seconds the APs will hit that.
Appears DNS servers that have been configured by Alta in /etc/config/https-dns-proxy are being used even after you manually configure your preferred servers in the UI. In my opinion, this shouldn’t happen. Especially DNS over TLS.
root@FamilyRoom:/etc/config# cat https-dns-proxy
config main ‘config’
option canary_domains_icloud ‘1’
option canary_domains_mozilla ‘1’
option dnsmasq_config_update ‘*’
option force_dns ‘0’
list force_dns_port ‘53’
list force_dns_port ‘853’
#Items below were commented out. Removed the comment to remove the bold font#
ports listed below are used by some
of the dnscrypt-proxy v1 resolvers
list force_dns_port ‘553’
list force_dns_port ‘1443’
list force_dns_port ‘4343’
list force_dns_port ‘4434’
list force_dns_port ‘5443’
list force_dns_port ‘8443’
#Items above were commented out. Removed the comment to remove the bold font#
option procd_trigger_wan6 ‘0’
config https-dns-proxy
option bootstrap_dns ‘1.1.1.1,1.0.0.1’
option resolver_url ‘https://cloudflare-dns.com/dns-query’
option listen_addr ‘127.0.0.1’
option listen_port ‘5054’
option user ‘nobody’
option group ‘nogroup’
config https-dns-proxy
option bootstrap_dns ‘8.8.8.8,8.8.4.4’
option resolver_url ‘https://dns.google/dns-query’
option listen_addr ‘127.0.0.1’
option listen_port ‘5053’
option user ‘nobody’
option group ‘nogroup’
config https-dns-proxy
option bootstrap_dns ‘208.67.222.222,208.67.220.220’
option resolver_url ‘https://doh.opendns.com/dns-query’
option listen_addr ‘127.0.0.1’
option listen_port ‘5055’
option user ‘nobody’
option group ‘nogroup’
root@FamilyRoom:/etc/config#
Looks like the following NTP servers are in use.
0.openwrt.pool.ntp.org
1.openwrt.pool.ntp.org
2.openwrt.pool.ntp.org
3.openwrt.pool.ntp.org
Source Information
system.ntp.enabled=‘1’
system.ntp.enable_server=‘0’
system.ntp.server=‘0.openwrt.pool.ntp.org’ ‘1.openwrt.pool.ntp.org’ ‘2.openwrt.pool.ntp.org’ ‘3.openwrt.pool.ntp.org’
Both DHCP-provided and integrated DOH servers are enabled in parallel on all Alta devices, in order to support local controllers behind networks that have DNS rebinding protection enabled (in general we recommend that this protection be disabled).
Both are not required to maintain a connection to the cloud; only one is, but it will still use both if possible.
Good catch on ping.alta.inc. All of our main web endpoints are AWS CloudFront endpoints, so the IPs will change and be dependent on your geographical location.
Would be useful from a user perspective to have these displayed in the GUI and allow user to choose there own. Not a fan predefined DNS and NTP.
The user ultimatedly should be able to configure key service NTP/DNS.
If you hve hardwired services please show these in the GUI , allow user to choose there preffered services.
The fact the user is not aware of the https proxy is not a good thing,
Can’t think of a router apart from ISP locked down one, where NTP and DNS are forced / locked down or hidden from from the user.
I concur. This is why I blocked anything not 53/udp. I could care less about the NTP traffic but do agree we should be able to configure ones of our choosing.
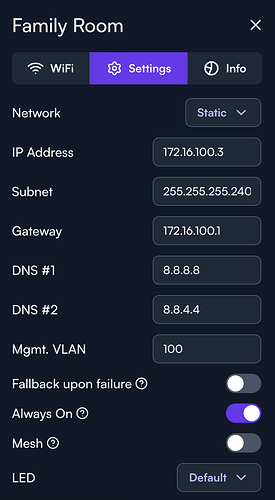
I don’t think I follow – you can configure DNS in the same place you edit the VLAN and subnet. Defaults are provided for convenience.
DNS HTTPS Proxy has hard coded DoT servers I think
Cloudflare, google and opendns.
NTP= openwrt pool
I’m talking about the statically pre-configured information I listed above on September 2nd.
Any updates on this topic?
We could make an official document, but is there anything missing from the above that you’d like on the article?
So far we have:
Required:
TCP Port 443 to the desired controller (cloud controller is manage.alta.inc)
TCP Port 443 for dl.alta.inc
One of these are required for time synchronization:
NTP (UDP Port 123)
HTTP/HTTPS (to 1.1.1.1, google.com, or alta.inc)
Optional:
HTTPS to CloudFlare/Google/OpenDNS DOH, for DNS-over-HTTPS
I think Alta should release an offical document.
Funny to find this thread immediately after searching for “Route 10 check which DNS servers are being used”.
It’s a surprise to find that going to https://www.dnscheck.tools/ shows a lot more results than expected.
It’s critical that end-users are aware of which DNS servers are configured in the background. As it stands, I have no idea if I have DoT or DoH working right now with the default configuration, and I want to be able to ensure that Route 10 is only hitting the DNS servers I specify.
Even though I provided my desired DNS overrides in my WAN settings, client DHCP on any VLAN also retrieves my ISP’s IPv6 DNS.
As of right now:
- What changes to configuration should be made to ensure that DHCP provides only the Route 10 as DNS resolver for both IPv4 and IPv6?
- How can the Route 10 be configured to proxy only the DNS servers listed in the WAN settings?
- How can DoT and/or DoH be set up?
@Alta-Chase is this on the roadmap in the near future?