Hello Everyone!
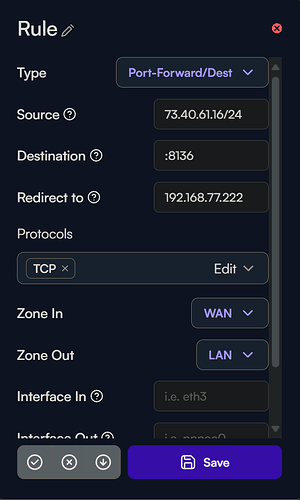
Just received my NFR kit today and I am having trouble getting my port forwarding to only allow the sources that I specify. Is there something I need to do beyond just creating a port forward rule with the sources I have listed? With what I have now, I can get to that port from any public address.
1 Like
A few things are not accurate here.
For source, if you want to allow this rule to apply to 73.40.61.16 and that address only, this field should be 73.40.61.16/32.
If, however, you want to allow the entire subnet, the proper source is 73.40.61.0/24. That will allow the entire /24 subnet.
It’s recommended that the “Redirect to” field includes the port as well. So this should be changed to 192.168.77.222:8136
Given that the source subnet is erroneous, it’s possible that field is ignored altogether, so that’s the one I’m questioning most.
1 Like
Thank you for the response. I had changed some settings from what the actual source addresses were since it was being posted here and mistyped that 16 at the end. It is meant to be the entire /24. I have also tried the redirect with both the port added and without.
The result is the same either way with me putting a /24 or /32 address as the source. Any source is still allowed
@davidrbatchelor1, I’m seeing the same thing.
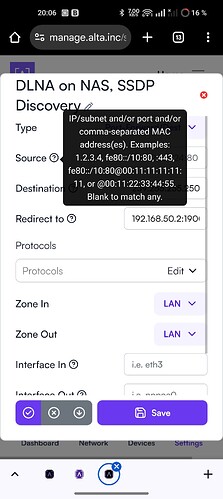
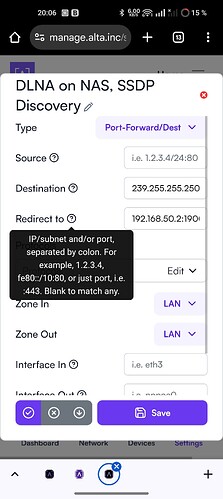
Just a little note here, the help says IP/subnet for Source and Redirect to, so one could argue that either a specific IP or subnet is supposedly valid syntax. Or have I misinterpreted the help pop-up:
Either way, there might be a bug that (erroneously) drops the input source IP (or subnet) so that is is actually not part of the redirect rule, as I mentioned here:
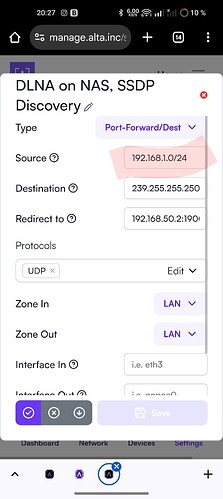
And just to highlight it again, if I set the source to e.g. 192.168.1.0/24,
there is still no trace of it in the firewall redirect settings (as would be expected?) when SSH to Route10 and:
uci show firewall | grep ‘.*redirect’
Output
firewall.@redirect[0]=redirect
firewall.@redirect[0].target=‘DNAT’
firewall.@redirect[0].name=‘DLNA on NAS, SSDP Discovery’
firewall.@redirect[0].proto=‘udp’
firewall.@redirect[0].src=‘lan’
firewall.@redirect[0].dest=‘lan’
firewall.@redirect[0].src_dport=‘1900’
firewall.@redirect[0].src_dip=‘239.255.255.250’
firewall.@redirect[0].dest_ip=‘192.168.50.2’
firewall.@redirect[0].dest_port=‘1900’
1 Like
Interesting, I hadn’t dug into the cli yet to check the rules, but that would make sense. I will check later to see if the source is being left off in the output for mine.
1 Like
My redirect rule seems to be missing the source information, as well:
root@Route10:~# uci show firewall | grep redirect
firewall.@redirect[0]=redirect
firewall.@redirect[0].target='DNAT'
firewall.@redirect[0].proto='tcp'
firewall.@redirect[0].src='wan'
firewall.@redirect[0].dest='lan'
firewall.@redirect[0].src_dport='8136'
firewall.@redirect[0].dest_ip='192.168.77.222'
firewall.@redirect[0].dest_port='8136'
1 Like
This might have been resolved in today’s Route10 firmware release, version 1.3x:
From what I see I now have the expected IP source in the redirect rule.
1 Like