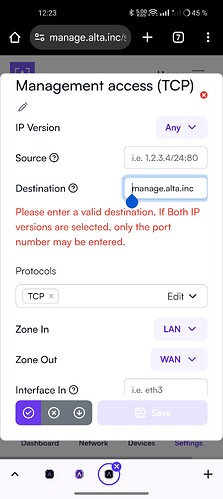
For the sake of fortifying the network, and opening up to the path to the cloud controller, what is the best practice to define outbound firewall rules in the UI according to https://help.alta.inc/hc/en-us/articles/29110607244571-Outbound-Firewall-Rules-Required? From what I can see the system does not allow for hostnames, but rather only explicitly entering the IPs.
I don’t think (personally) I have ever seen a firewall support hostnames for firewall rules as it would be a lot slower.
The hostnames just mean they need to be allowed (if you do blocking based on domains using say proxy)
The instruction is probably targetted at scenarios where Route 10 is installed in an enviroment with a dedicated firewall infront. FQDN allow/block lists may be used so in specfic cases you;d need to ALLOW access to the Alta domians/ports/
WAN <—> FIREWALL <—> Route 10 <——>.Network
Unless you have something infront of the Route 10 , nothing more to do.
In most use cases not an issue.
Ah, I see. ![]() I don’t have definitive need for this, just playing around and was pondering on if and how one would be able to tighten the firewall while still ensuring access to the cloud controller in a dynamic way with the Route10. I will not bang my head for this
I don’t have definitive need for this, just playing around and was pondering on if and how one would be able to tighten the firewall while still ensuring access to the cloud controller in a dynamic way with the Route10. I will not bang my head for this ![]()